The 9 Steps to DPA Heaven : Step 9: Report Any Security Breaches
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Welcome to the last part of of this Nine Steps to Data Protection Heaven article.
In the previous sections, we covered the setup and operations of your Data Protection programme. In this last article, we will look at Step 9, and what you should do when a breach occurs.
But before we get started, we will just recap on the process so far:
- In Step 1 we looked at how we should "Implement a data protection policy",
- Step 2 then covered the key activities around the DPIA.
- Step 3 looked at how and why you should appoint a Data Protection Officer.
- Step 4 covers the obligations around Staff training.
- In Step 5, we covered how we should ensuring valid consent for processing,
- with Step 6 covering privacy notices.
- In Step 7 we looked at how we should **implement technical measures **( or controls ), and finally
- In Step 8 we looked at the steps in supporting subject access requests,
The details and further information around all Steps can be found in the links provided below. Links to the Audio versions should be also available at the bottom of this article.
Links
- You can listen to this Step 9 as a podcast here, or
- the complete audio (parts1-9) here.
- The complete article is available here.
- If you have missed any part or would like to start from the beginning, you can find links to all sections at the bottom of this article.
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Here is a summary of the 9-Step process, that you can follow as we walk through each step.
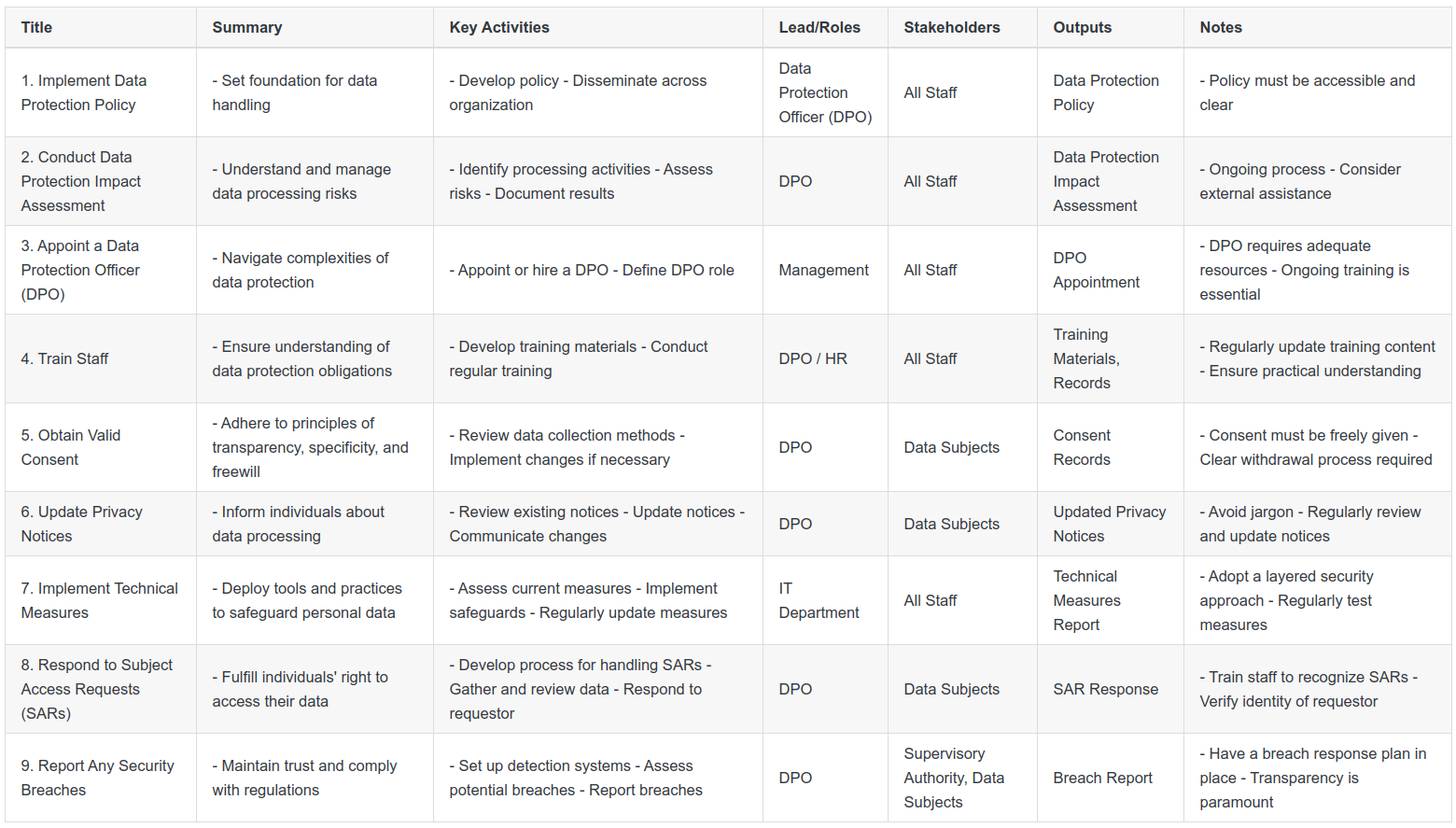

Step 9: Report Any Security Breaches

"The unfortunate reality of the digital age is that data breaches occur. What's important is how your organisation responds. GDPR requires organisations to report certain types of personal data breaches to the relevant supervisory authority. Here's how you can ensure compliance and maintain trust in your data protection strategy:
Key Activities
The first key activity is to set up systems to detect and monitor for security breaches. This could involve using software tools, conducting regular security audits, or training staff to recognize potential breaches.
When a potential breach is detected, it's important to swiftly assess the situation. Determine the nature and extent of the breach, and the potential impact on personal data and individuals' rights and freedoms.
If the breach poses a risk to these rights and freedoms, you must report it to your relevant supervisory authority. This report must usually be made within 72 hours of becoming aware of the breach.
Moreover, if the breach poses a high risk to individuals, you may also need to inform them directly. This notification should be clear and concise, and provide information on the nature of the breach, the likely consequences, and what measures have been or will be taken.

Key Roles and Stakeholder Engagement
The Data Protection Officer (DPO) or data protection lead typically oversees this process, but IT staff, HR, and management also play critical roles in detecting, investigating, and managing breaches. The relevant supervisory authority and affected individuals are the key stakeholders in this process.
Outputs
The key outputs from this step are the breach report submitted to the supervisory authority and the notification to affected individuals, if required. Also, keep a record of all breaches, regardless of whether they were reported, to inform future risk assessments and security measures.

Summary
One key piece of advice is to have a breach response plan in place. This helps ensure a quick, coordinated, and effective response when a breach occurs.
Regular training can also help staff understand the types of incidents that need to be reported and how to report them.
Transparency is paramount when handling data breaches. It's not only a regulatory requirement but also crucial for maintaining trust with individuals and mitigating reputational damage.
In conclusion, the ability to effectively respond to and report data breaches is a key part of any data protection strategy. Through prompt and transparent actions, you can uphold your legal obligations and demonstrate your commitment to data protection.

Conclusion: Ascending to Data Protection Heaven
Embarking on the journey of data protection can seem daunting, but when broken down into manageable steps, it becomes much more achievable. The nine-step process we have just outlined is your stairway to "Data Protection Heaven."
We started with implementing a robust data protection policy, setting the foundation for how your organisation handles personal data. The second step was to conduct a Data Protection Impact Assessment, ensuring you understand and manage the risks associated with data processing.
The third step was to appoint a Data Protection Officer (DPO), a crucial figure who navigates the complexities of data protection on behalf of your organisation. Following this, we stressed the importance of ensuring all staff members understand their obligations regarding data protection, achieved through comprehensive training and clear communication.
Step five outlined the necessity of obtaining valid consent for processing personal data, adhering to the principles of transparency, specificity, and freewill. In step six, we emphasized the importance of keeping your privacy notices up to date, ensuring individuals are well-informed about their data processing.
Our seventh step focused on implementing technical measures, deploying tools, and practices to safeguard personal data from unauthorized access and accidental loss. In step eight, we learned about responding to subject access requests, fulfilling individuals' right to access their data.
Finally, the ninth step involved the reporting of any security breaches, reinforcing the importance of transparency and immediate action in maintaining trust and complying with regulations.
These steps provide a systematic approach to meeting Data Protection requirements, offering a comprehensive yet straightforward framework for those tasked with managing personal data. They are not just for Data Protection Officers or IT professionals but for anyone in an organisation who interacts with personal data.

Through following these steps, your organisation can comply with legal requirements, reduce the risk of breaches, maintain trust with customers and stakeholders, and ultimately, create a secure data environment. Each step brings you closer to your destination: a state of data protection nirvana, or as we have playfully titled it, "Data Protection Heaven."

The road may have its complexities, but by adhering to this process, you make the journey a manageable and rewarding experience. Welcome to Data Protection Heaven, where compliance, trust, and security live in harmony. Safe travels on your data protection journey!
You can find links to the complete Article and the serialised version of this article in the links below. You can find more useful guidance and links to further articles on Risk Management and Data Protection at https://www.riskmanage.io
Navigation
Parts/Steps
- Implementing a data protection policy,
- Carrying out a data protection impact assessment,
- Appointing a Data Protection Officer,
- Making sure our staff understand their obligations,
- Ensuring valid consent for processing,
- Updating privacy notices, and
- Implementing technical measures,
- Respond to Subject Access Requests.
- Report Any Security Breaches.
Links to the complete list of audio podcasts for this series are available here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7, Part 8, Part 9, Parts1-9/Complete
If you like this content, find it useful or are looking for further assistance, you can contact us via info@riskmanage.io, webchat or via our website using the links provide.