The 9 Steps to DPA Heaven : Step 2 - Conduct Data Protection Impact Assessment (DPIA)
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Welcome to Step 2, The Data Protection Impact Assessment, where we will look at the DPIA and why it is an essential part of your data protection toolkit. In Step 1, we covered Data Protection Policy and how it remains a crucial step on your DP journey, it sets the tone, direction, and the handrail for all data-related activities.
Links
- You can listen to this Step 2 as a podcast here, or
- the complete audio (parts1-9) here.
- The complete article is available here.
- If you have missed any part or would like to start from the beginning, you can find links to all sections at the bottom of this article.
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Here is a summary of the 9-Step process, that you can follow as we walk through each step.
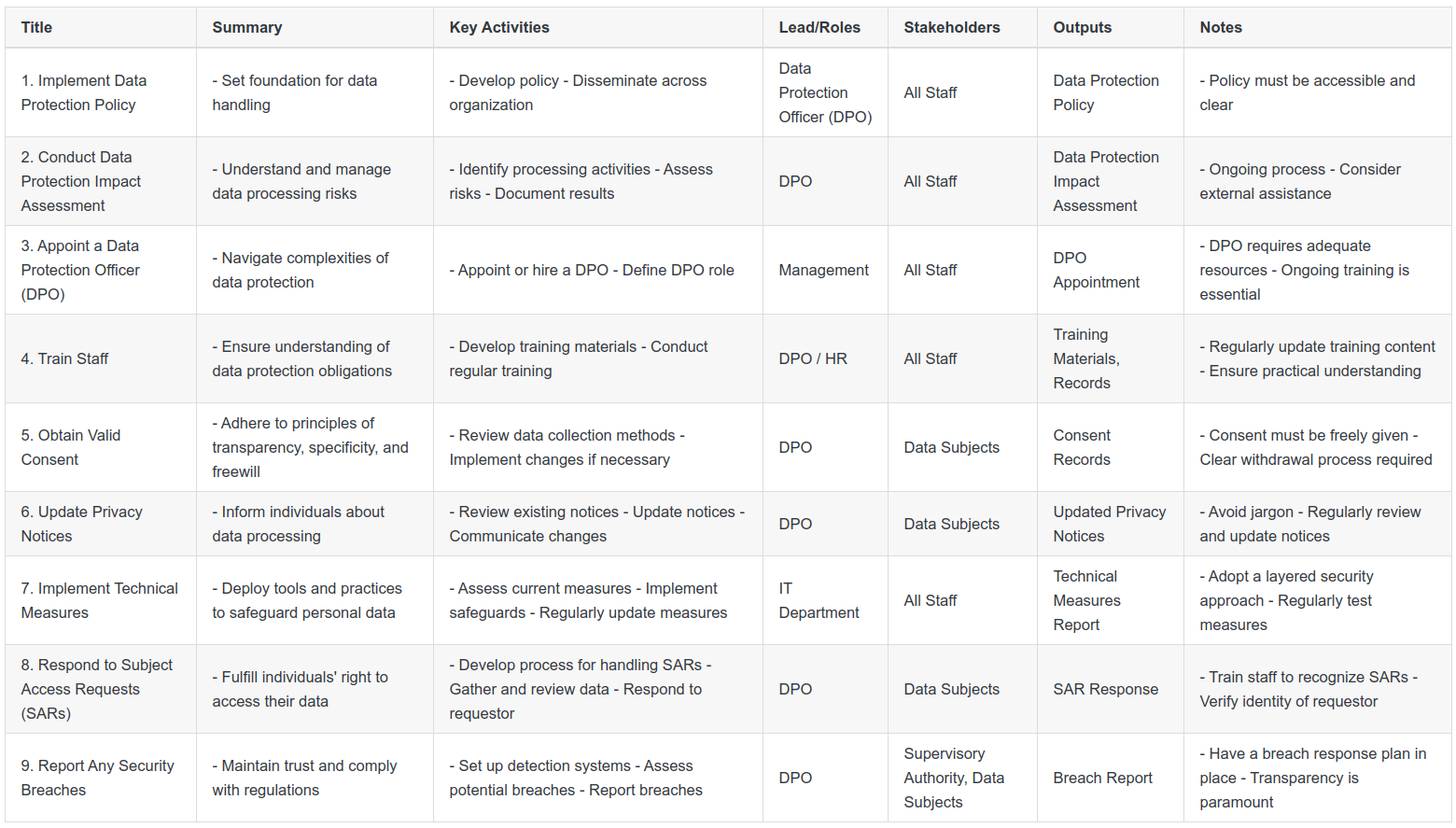

Step 2: Carry Out a Data Protection Impact Assessment

The Data Protection Impact Assessment (DPIA) is an essential instrument in your data protection toolkit, particularly when it comes to high-risk data processing scenarios. It provides a structured method to analyze, identify and minimize the data protection risks of a project or plan.
Key Activities
Carrying out a DPIA involves several distinct activities. Firstly, it's important to describe the nature, scope, context, and purpose of the data processing. This gives a clear picture of what exactly you're assessing and lays a solid foundation for the rest of the process.
Next, assess the necessity and proportionality of the processing. This means ensuring that you're only processing data that is necessary to achieve your purpose and that you're not holding onto it for longer than needed.
Subsequently, identify and assess the risks to individuals. This could range from potential threats to their privacy, to potential misuse of their data, and even the risk of data breaches.
Finally, identify measures to mitigate those risks. These could be anything from technical measures like encryption, to policy measures such as limiting access to the data.

Key Roles and Stakeholder Engagement
The key stakeholders in carrying out a DPIA are the Data Protection Officer (DPO), who oversees the assessment, and the project team, who will need to understand the outcomes of the DPIA and implement the necessary measures. It may also be necessary to consult with individuals (or their representatives) whose data will be processed, to gain their perspectives on the proposed processing.
Outputs
The primary output from this step is the DPIA report. This document should provide a thorough overview of the data processing operation, highlight potential risks, and propose mitigation measures. This report should be updated regularly, especially if there are changes in the processing operation that may affect the risk to individuals.
 Summary
Summary
From our experience, one of the best practices when carrying out a DPIA is to start early and update often. It's much easier to address data protection risks during the design stage, rather than retrofitting solutions after a system or process is already in place. This is what's often referred to as "privacy by design."
Another tip is to make sure that you're being thorough in your risk assessment. This includes considering both the likelihood and the severity of any potential impact on individuals. Keep in mind that even low-risk scenarios can have a significant impact if they are likely to occur frequently.
Furthermore, don't underestimate the value of external input. Whether it's consulting with data protection experts or seeking the views of the individuals whose data you're processing, these perspectives can help identify risks and solutions that you might not have considered.
Remember, a DPIA isn't just a box-ticking exercise to meet regulatory requirements; it's a valuable tool to help you process data in a way that respects individuals' rights and minimizes risks. By taking the time to carry out a thorough DPIA, you can ensure that your data processing operations are not only compliant, but also more likely to earn the trust of the individuals whose data you're handling.
In Step 3, we will cover the appointment of the Data Protection Officer , and how they serve as a critical figure in overseeing and ensuring compliance within your organisation.
Navigation
- The next part, "Step 3: Appoint a Data Protection Officer (DPO)" is available here.
- Step 3 Audio podcast available here
- Links to the complete list of audio podcasts for this series are available here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7, Part 8, Part 9, Parts1-9/Complete
- Links to each Section: Step 1, Step 2, Step 3, Step 4, Step 5, Step 6, Step 7, Step 8. Step 9.
If you like this content, find it useful or are looking for further assistance, you can contact us via info@riskmanage.io, webchat or via our website using the links provide.