The 9 Steps to DPA Heaven : Step 7 - Implement Technical Measures
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Welcome to Step 7 of The Nine Steps to Data Protection Heaven . In the previous article, Step 6, we covered Privacy Notices, and the important part they play in delivering against your requirements. In Steps 1 to 5 , we covered : **- Implementing a data protection policy,
- Carrying out a data protection impact assessment,
- Appointing a Data Protection Officer,
- Making sure our staff understand their obligations, and ,
- Ensuring valid consent for processing.**
In Step 7, we look at the wide topic of Implementing the Technical Measures, which include software, processes and technology, providing preventative, detective or corrective controls.
The details and further information around all Steps can be found in the links provided below. Links to the Audio versions should be also available at the bottom of this article.
Links
- You can listen to this Step 7 as a podcast here, or
- the complete audio (parts1-9) here.
- The complete article is available here.
- If you have missed any part or would like to start from the beginning, you can find links to all sections at the bottom of this article.
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Here is a summary of the 9-Step process, that you can follow as we walk through each step.
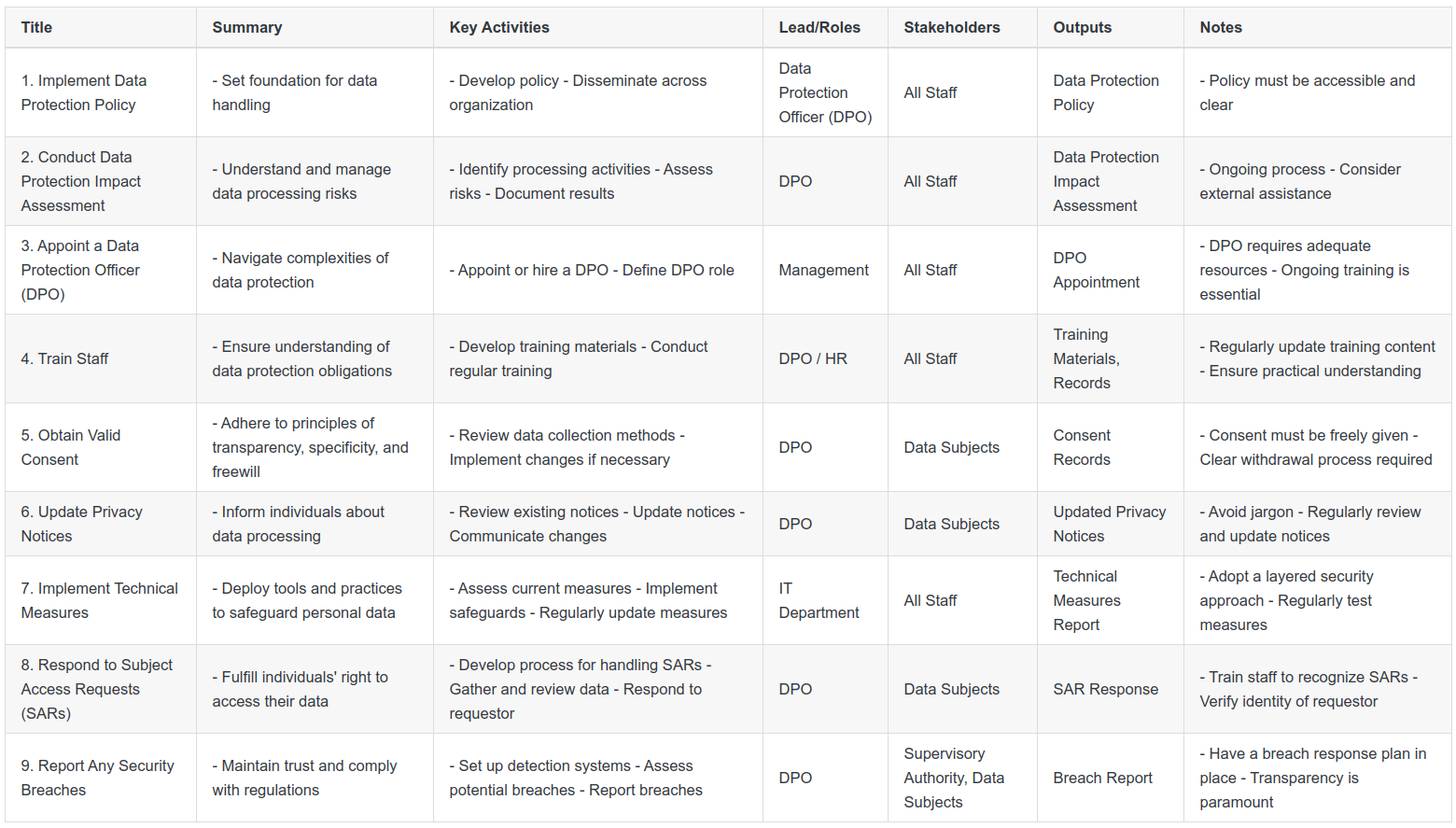

Step 7: Implement Technical Measures

Technical measures are the backbone of any data protection strategy. They include the tools, systems, and practices that protect personal data from unauthorized access, unlawful processing, accidental loss, destruction, or damage. This step involves setting up and maintaining these measures to ensure robust data security.
Key Activities
Begin by assessing your current technical measures and identifying any gaps or vulnerabilities. This can be done through activities like risk assessments or penetration testing.
Next, implement necessary safeguards. These may include access controls to limit who can access personal data, encryption to protect data during transmission and at rest, and secure data disposal methods. Also, consider implementing intrusion detection systems and firewalls to protect against external threats.
Regular data backups are crucial to prevent data loss in case of accidents or system failures. Ensure you have a robust backup system in place that copies and stores data securely.
Lastly, maintain and regularly update these technical measures. This includes regular software updates, security patches, and system reviews to ensure continued data protection.
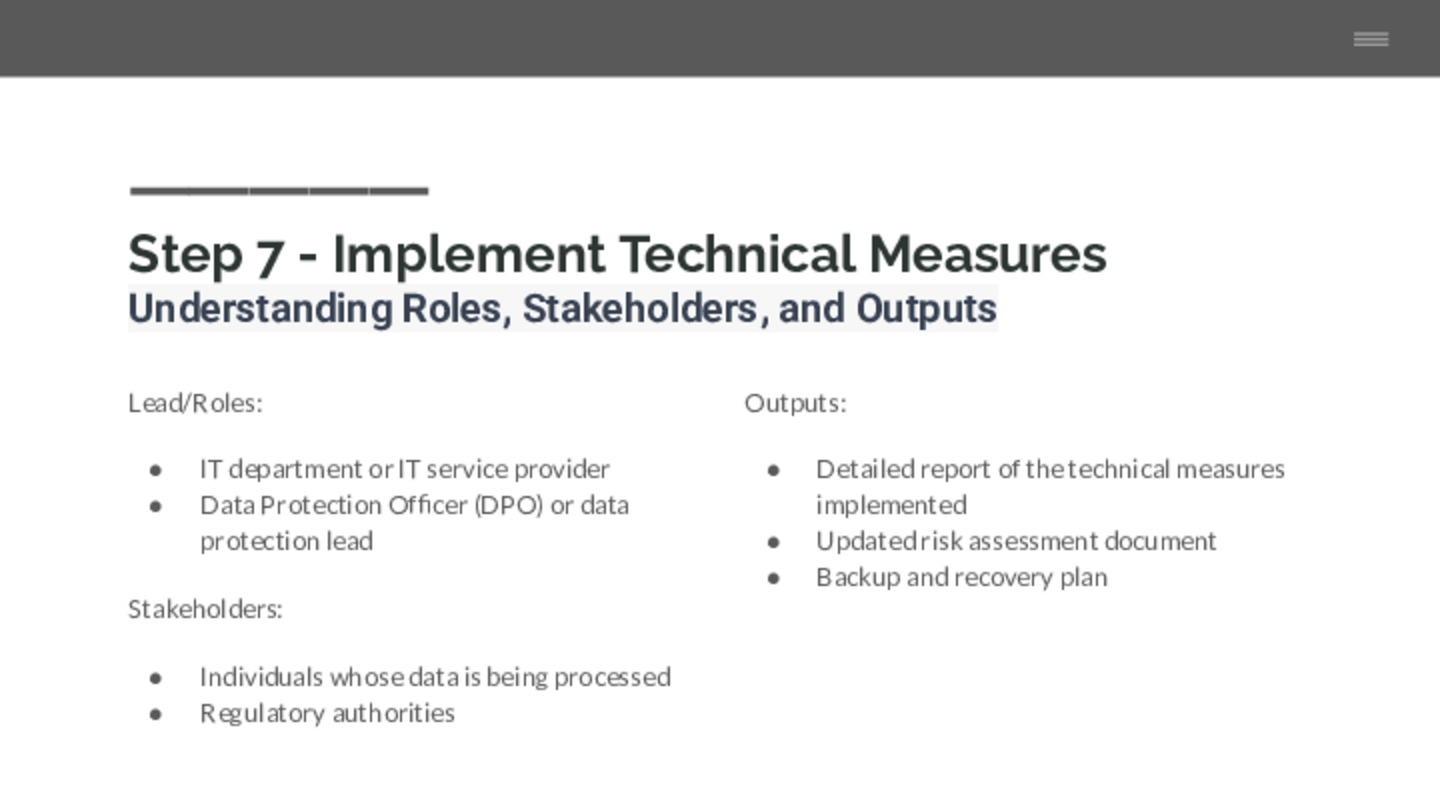
Key Roles and Stakeholder Engagement
This step involves your IT department or IT service provider, who will be responsible for implementing and maintaining these technical measures. The DPO or data protection leads should oversee this process to ensure it meets data protection requirements.
Outputs
The outputs from this step include a detailed report of the technical measures implemented, an updated risk assessment document reflecting the reduced risk due to these measures, and a backup and recovery plan. Records of regular maintenance activities and software updates should also be kept as proof of ongoing data protection efforts.
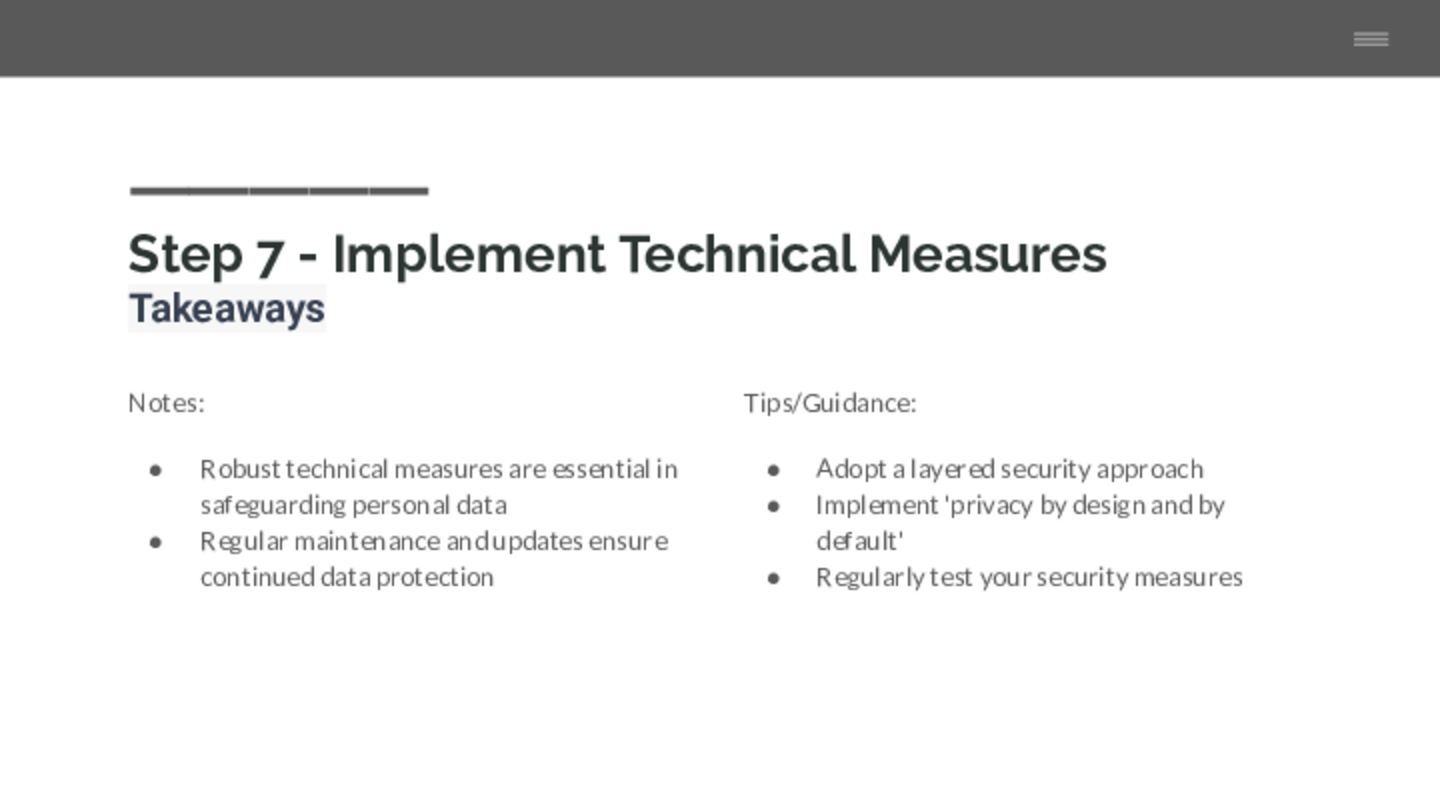
Summary
One best practice is to adopt a layered security approach. Don't rely on a single measure to protect your data; use a combination of measures to provide multiple barriers against threats.
Another tip is to implement 'privacy by design and by default'. This means considering privacy at the initial design stages of any new system, service, or process that involves personal data.
Remember to regularly test your security measures, including your backup and recovery systems. This can help you identify any weaknesses before they can be exploited and ensure your systems are working as expected.
Lastly, make sure your technical measures align with your data protection policies. They should work together to provide a comprehensive and effective data protection strategy.
In conclusion, implementing robust technical measures is essential in safeguarding personal data and maintaining trust in your organisation. With these controls in place, you can confidently assure individuals that their data is safe in your hands.
In the next section, Step 8, we will cover Subject Access Requests , and how to integrate them into your normal service operations.
Navigation
- The next part, "Step 8: Respond to Subject Access Requests" is available here.
- Step 8 Audio podcast available here
- Links to the complete list of audio podcasts for this series are available here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7, Part 8, Part 9, Parts1-9/Complete
- Links to each Section: Step 1, Step 2, Step 3, Step 4, Step 5, Step 6, Step 7, Step 8. Step 9.
If you like this content, find it useful or are looking for further assistance, you can contact us via info@riskmanage.io, webchat or via our website using the links provide.