The 9 Steps to DPA Heaven : Step 8 - Respond to Subject Access Requests
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Welcome to Step 8 of The Nine Steps to Data Protection Heaven article. In previous 7 Steps we covered
- Implementing a data protection policy,
- Carrying out a data protection impact assessment,
- Appointing a Data Protection Officer,
- Making sure our staff understand their obligations,
- Ensuring valid consent for processing,
- Updating privacy notices, and
- Implementing technical measures,
In Step 8, , we will look at how to Respond to Subject Access Requests.
Links
- You can listen to this Step 8 as a podcast here, or
- the complete audio (parts1-9) here.
- The complete article is available here.
- If you have missed any part or would like to start from the beginning, you can find links to all sections at the bottom of this article.
A roadmap to effectively safeguard personal data, ensure regulatory compliance, and build lasting trust with stakeholders.
Here is a summary of the 9-Step process, that you can follow as we walk through each step.
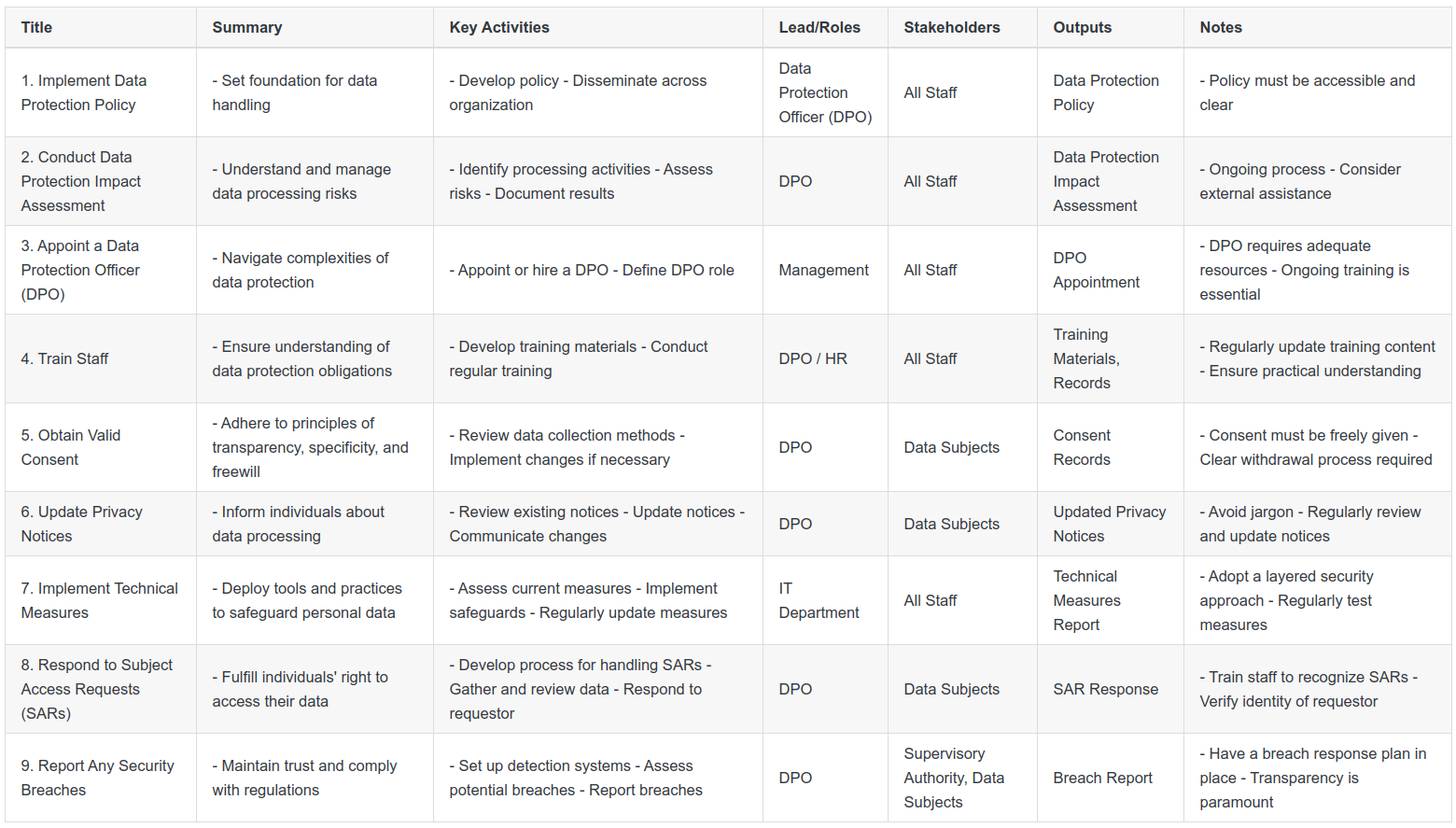

Step 8: Respond to Subject Access Requests

A fundamental aspect of data protection is allowing individuals to understand what personal data you hold about them. This is often done through subject access requests (SARs), which require efficient and accurate handling. Here's how you can effectively manage this process:
Key Activities
The initial step is to develop a streamlined process for recognizing and handling SARs. An SAR can be made through any channel, so it's essential that all staff members understand what these requests look like and how they should be processed.
Once a request is identified, it should be forwarded to the relevant team or person for handling, often the Data Protection Officer (DPO) or designated data protection lead.
This person should then locate the relevant data, ensuring all requested information is gathered. This process may involve searching databases, email records, and physical files.
After the data is gathered, review it to ensure it can be released. Sometimes, data might include information about other individuals or sensitive business information that cannot be shared.
Finally, respond to the requester with the data in a concise, transparent, and easily understandable format, usually within one month of the request being made.

Key Roles and Stakeholder Engagement
Key roles include frontline staff who may receive SARs, the DPO or data protection lead who handles the request, and IT staff who may need to assist with data retrieval. The key stakeholder here is the individual making the SAR.
Outputs
The main output from this step is the response to the SAR. This should include all the requested information that can be shared, as well as any necessary explanations or context. Also, a record of the SAR and its response should be kept for future reference or in case of disputes.
 Summary
Summary
Training your staff to recognize an SAR is crucial. SARs do not have to be made in a specific format or even explicitly state that they are SARs.
Another best practice is to verify the identity of the requester before providing the information to prevent unauthorized disclosure of personal data.
It's also a good idea to establish a centralized system for managing SARs. This can help streamline the process, prevent delays, and ensure a consistent response.
Remember that a reasonable fee can only be charged for repetitive or unfounded requests. For most SARs, you should provide the information free of charge.
In conclusion, effectively managing SARs is not only a legal requirement but also a chance to demonstrate your organisation's commitment to transparency and individual rights. With a well-planned and executed process, you can turn SARs into a positive experience for both your organisation and the individuals involved.
In the final step, Step 9, we will look at reporting, and understand when, and how, you need to inform your stakeholders, and the ICO.
Navigation
- The last part, "Step 9: Report Any Security Breaches" is available here.
- Step 9 Audio podcast available here
- Links to the complete list of audio podcasts for this series are available here: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7, Part 8, Part 9, Parts1-9/Complete
- Links to each Section: Step 1, Step 2, Step 3, Step 4, Step 5, Step 6, Step 7, Step 8. Step 9.
If you like this content, find it useful or are looking for further assistance, you can contact us via info@riskmanage.io, webchat or via our website using the links provide.